Microsoft published an important new article today detailing some of the requirements and recommendations for upgrading Exchange Server to the latest version, Exchange Server SE (Subscription Edition). Upgrading your organization from current versions to Exchange Server SE - Microsoft Community Hub
This article applies to all customers running Exchange Server on-premises, including hybrid customers using Exchange Server for hybrid management.
The blog post is dense with a lot of information, but the key important points are:
- Exchange Server SE is the next version of Exchange
Server and will be released the second half of 2025.
- Exchange 2019 CU15 will be released Q4 this year. This
will be the last cumulative update for Exchange 2019. There will be no
future updates for Exchange 2016.
- Exchange 2019 CU15 will allow for an in-place upgrade
to Exchange Server SE. This is a first for Microsoft. Previous upgrades
required new servers.
- Exchange Server SE will only allow coexistence with
Exchange 2016 CU23 and Exchange 2019 CU14/15.
- Exchange 2013 will become totally unsupported with the
release of Exchange 2019 CU15.
You must upgrade or remove Exchange 2013 from your organization ASAP.
- Customers should upgrade their Exchange 2016 servers to
Exchange 2019 CU14/15 ASAP to prepare for Exchange Server SE.
- After Exchange Server SE is released in 2025, Exchange
2016 and 2019 will be subject to throttling by Microsoft. See Throttling
and Blocking Email from Persistently Vulnerable Exchange Servers to
Exchange Online - Microsoft Community Hub
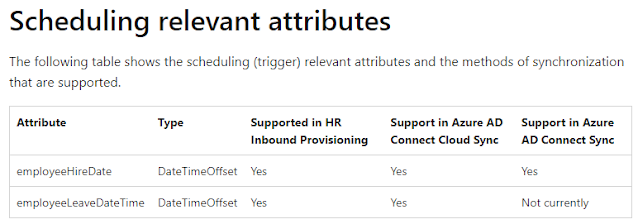
- The following table from the blog post illustrates the
milestones and actions to take:
- Licensing for Exchange Server SE will be similar to
Exchange 2019 – You either must have an existing Microsoft 365 license for
all users or you can buy server licenses and CALs with Software Assurance
(SA).
Please reach out to EXPTA Consulting if you need help implementing these requirements. We also can meet with you to discuss options for removing the last Exchange Server from hybrid environments.